Olminator is a simple conversion utility: it takes one input file (.olm) – which you provide – and creates a number of output files (.mbox, .ics, .vcf) in the process that are written to an output folder – which you also provide.
It fully complies with Apple's "sandboxing" requirements for Mac applications – otherwise it wouldn't be in the AppStore anyways.
In particular, Olminator does ...
Instead, you control ...
What happens on your computer, stays on your computer!
Hint: Since your emails, calendar items, contacts and notes are data privacy-relevant items, make sure to not have them sit around unprotected on a memory stick or an external drive. Delete export files (.olm) and conversion output (.mbox, .ics and .vcf) after you've successfully imported your content into the target applications – or make sure you've stored them in a safe and secure place.
Olminator does not make use of any Internet connectivity except for two reasons or use-cases which are described in detail below. All such cases can be switched off in the Settings section if you don't feel comfortable about them.
The first exception to the above rules of not accessing system resources is the Automatic version check of Olminator.
In order to determine whether there is a newer version available for download on the Apple App Store than you have currently installed, Olminator may issue exactly two HTTP requests each time it gets started. The first one goes to the Apple App Store API and retrieves the version info of the latest version of Olminator available in the App Store for download. The second request goes to the Olminator support website where it retrieves the latest version of the release notes for Olminator, describing what new features, changes to existing features or bug fixes can be found in which version. Responses to those two requests are then used to determine whether Olminator displays information to you about the availability of a new product version available for download. There are no other network requests issued and there is no information transferred from your Mac to either of these sites besides the implicit fact that apparently Olminator was started and an HTTP request was sent from some IP address (the external IP address your Internet provider has currently assigned to your access point to their network). There is no (!) personal data transferred.
Hint: Please be aware that starting with version 2.02, the above automatic request to both the Apple API as well as goerke.tech when starting Olminator can also be switched off completely in Olminator's Configuration tab under "General settings" – just in case you still have any concerns about the fact.
Here are the two static HTTP requests issued by Olminator for your reference. Feel free to check those out for yourself – it's two JSON-formatted documents being linked.
Hint: Don't be surprised: your browser will not open the content in a window, but download the JSON file as a text document into the downloads folder of your browser
The second exception to the above rule of not accessing system resources is the retrieval of remote Web content which may be referenced from within your emails' or calendar items' content.
Your emails or calendar appointments will likely contain an HTML-formatted email or appointment "body". Commercial emails, like e.g. an order confirmation of an online shopping site, may contain references to external Web content as part of this message's body (an order confirmation may list all products ordered, each product with the corresponding product image linked from within the email). In order to reproduce the content of emails and calendar appointments in the best possible manner, Olminator needs to retrieve those externally referenced Web resources by loading them via HTTP over the network if the email or appointment gets displayed in the item preview of the Viewer or gets converted to PDF. The same holds true for Microsoft Outlook or Apple Mail – they retrieve the content over the Internet, too. If the remote content doesn't get loaded, the email or calendar item content may not be properly displayed or rendered, or may show broken links.
Obviously, allowing the retrieval of such referenced content via HTTP means exposing information to the referenced remote Web site, specifically the fact that e.g. ...
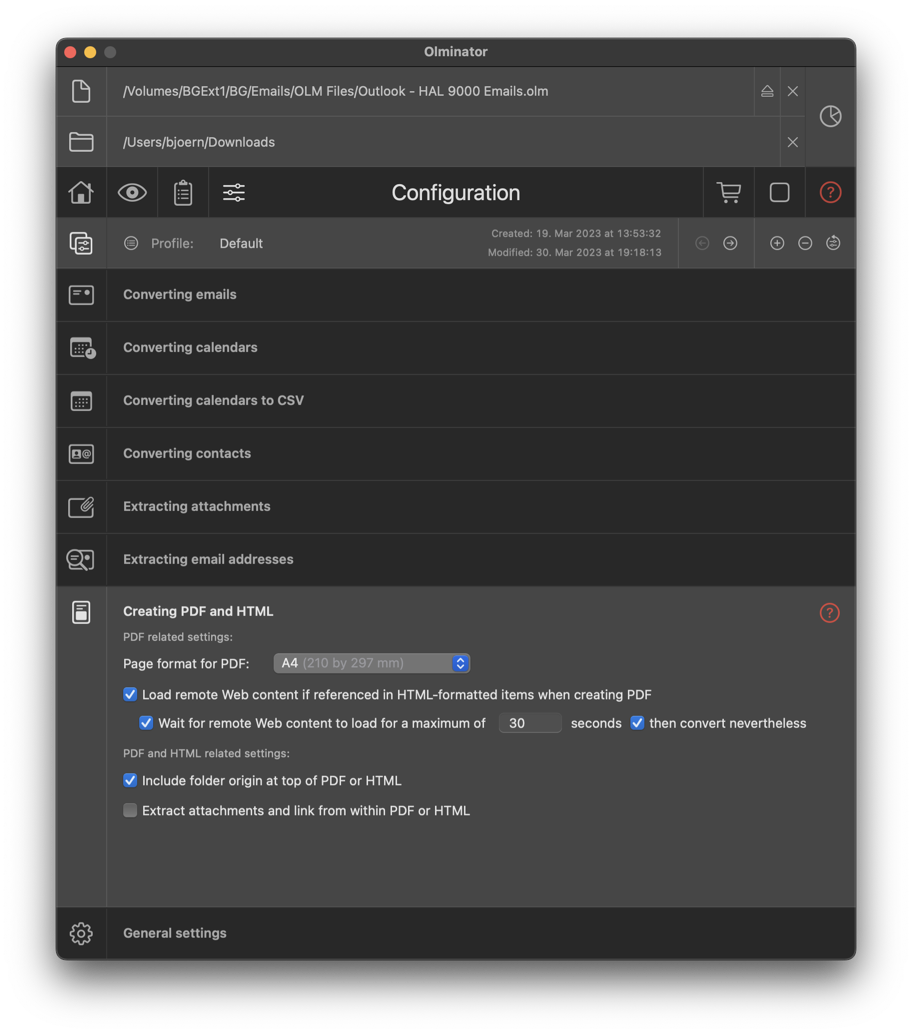
Since not everyone feels comfortable exposing such information to remote Web sites, Olminator allows you to accordingly disable the retrieval of remote Web content. Here's how to control the retrieval:
Caveat: By default, this option is enabled, which means your PDFs will be generated with as many external Web content references being resolved as possible. Once this Web content has been downloaded, it will be embedded into the generated PDFs, i.e. opening the PDF will not once more go out into the Internet for loading!
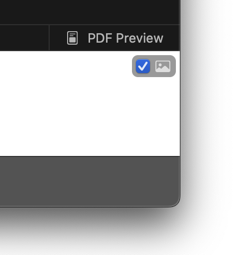
Hint: If you want to load the remote Web content of just the currently displayed item, click on the little "image" icon next to the checkbox – Olminator will then load the remote Web content for the current item just once and not change the general setting for loading remote Web content for any other item.